wELCOME tO eMVTRACKERA SmALL EMV HaCKTOoLZ LANDScAPE BROUGHt tO YOU BY CYBERCRiME tRACKER
Rotate your phone for a better viewing experience.
EMV MALWARE NOTiCE
SHA-256: 6cb6a3e75965ebacf1f6d72096a90e9d80be6d1c9d6ebd7dd9453992140a9d5c - VT
SHA-1: 1a72b1c303ee3ca79aed16da22f97ce563f01e2f
File type: EXE/Windows
File size: 15.46 MB
File name: MainApplication.exe
ProtectionID:
Compilation date: 2015-08-07 18:04:19
First seen: 2020-12-19 08:00:33
Name: X2A (mr_emv trial)
Actor: mr_emv
Additional note: Serial:
LVUWAQOAAAA+oBurz1nigC5dfztwldBKtJIIXFAZH+rqw1QYPe5BR8Uq8C0qF9wQ
jCAtsSZWz4LHBKFe6JQnROIJJ20gg2eGHWHtfHXy8MhKMrWHqmpiAv6YAoUAfVXp
ru6OyEaViAbmwYUtq1uVPIrKklIHSOFkOFSYhu863c/lcGlKJWGNFTKPf1lAQTqL
GHPpRl32r7swgLuUvIG81/7iL6xlDWef1dugvIhHR/0/+QaSC7d3E6OL/VcjZwpZ
RrHtTM2641ltooytOfnfjE+siFT3NEnoj+k04HpjER5RrLLVgbHUz5pFpMK799yX
vQ/hGxywRIGAAAAA
Similar to 10d8998094e9bdd9951a2edcc9cec3540628712b325682b21dba02b6650d97c9.
From the same family: X1 v1.1, X1 v1.1, X1 Toronto.
Cosmetic reshacks from the 'x2 cartel':
X1 v4.1, X1 v5.0, X2G, X2A, X2A (nfc design), X2A Cracked, X2, X2.EMV.
Screenshot:
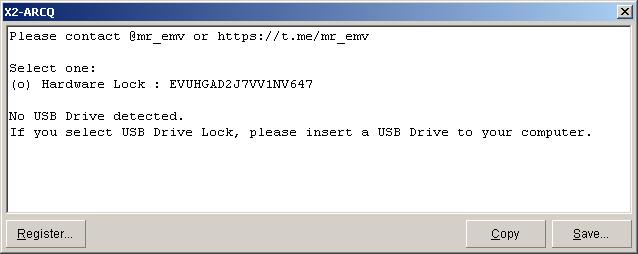
Mirror provided by vx-underground.org, thx!
(infected)
SHA-1: 1a72b1c303ee3ca79aed16da22f97ce563f01e2f
File type: EXE/Windows
File size: 15.46 MB
File name: MainApplication.exe
ProtectionID:
[CompilerDetect] -> Borland Delphi (unknown version) - 60% probability
Compilation date: 2015-08-07 18:04:19
First seen: 2020-12-19 08:00:33
Name: X2A (mr_emv trial)
Actor: mr_emv
Additional note: Serial:
LVUWAQOAAAA+oBurz1nigC5dfztwldBKtJIIXFAZH+rqw1QYPe5BR8Uq8C0qF9wQ
jCAtsSZWz4LHBKFe6JQnROIJJ20gg2eGHWHtfHXy8MhKMrWHqmpiAv6YAoUAfVXp
ru6OyEaViAbmwYUtq1uVPIrKklIHSOFkOFSYhu863c/lcGlKJWGNFTKPf1lAQTqL
GHPpRl32r7swgLuUvIG81/7iL6xlDWef1dugvIhHR/0/+QaSC7d3E6OL/VcjZwpZ
RrHtTM2641ltooytOfnfjE+siFT3NEnoj+k04HpjER5RrLLVgbHUz5pFpMK799yX
vQ/hGxywRIGAAAAA
Similar to 10d8998094e9bdd9951a2edcc9cec3540628712b325682b21dba02b6650d97c9.
From the same family: X1 v1.1, X1 v1.1, X1 Toronto.
Cosmetic reshacks from the 'x2 cartel':
X1 v4.1, X1 v5.0, X2G, X2A, X2A (nfc design), X2A Cracked, X2, X2.EMV.
Screenshot:

Mirror provided by vx-underground.org, thx!
(infected)
...83fab200.zip
21-10-24
...b928e1f7.zip
21-08-07
...be8a79c9.zip
21-07-17
...0393ebfd.zip
21-06-12
...c6a1ec78.zip
21-06-05
...b2fefd36.zip
21-05-23
...b58f906f.zip
21-05-22
...8c55884d.zip
21-05-22
...a4cbe72a.zip
21-05-21
...6472a452.zip
21-05-18
...be8a79c9.zip
21-07-17
...83fab200.zip
21-10-24
...b928e1f7.zip
21-08-07
...0393ebfd.zip
21-06-12
...c6a1ec78.zip
21-06-05
...f2874124.zip
14-09-04
...c7ebe762.zip
18-01-19
...8c55884d.zip
21-05-22
...b2fefd36.zip
21-05-23
...b58f906f.zip
21-05-22
MOST ViEWED NOTiCE
EMVToolUltimate v1.0
9442
CATR 3.8.7
8907
X2 v2.8
7360
ATRToolUltimate 1.0
5342
POS Simulator 2.0
5263
ATRtool v2.0
5081
Emvfoundry v1.0.0.63
4663
POS Simulator 2.0
3808
X2.EMV
3750
emvfoundry v1.0.0.54
3439
Daphne
3111
Emvfoundry v1.0.0.19
3056