wELCOME tO eMVTRACKERA SmALL EMV HaCKTOoLZ LANDScAPE BROUGHt tO YOU BY CYBERCRiME tRACKER
Rotate your phone for a better viewing experience.
EMV MALWARE NOTiCE
SHA-256: 14ca877b444ae0d4d0bfd7709da763ff4c1434a73bc3d15251101facd33f7d83 - VT
SHA-1: 4c740df32ceb14e93294855d124b47440a558571
File type: EXE/Windows
File size: 2.19 MB
File name: Internal.exe
ProtectionID:
PDB/VBP pathway: g:\dev\_current\smart card reader\X1_software\softwares\internal full\Src\X1\Release\X1.pdb
Compilation date: 2015-08-08 16:30:16
First seen: 2015-08-08 16:30:16
Name: X1 v1.1
Additional note: Code: cf4ac1badfd87b60e9e81987a9959a18a6791c9ba5070e7980efd624dc75bc38.
From the same family: X1 v1.1, X1 Toronto.
Cosmetic reshacks from the 'x2 cartel':
X1 v4.1, X1 v5.0, X2G, X2A, X2A (nfc design), X2A (mr_emv trial), X2A Cracked, X2, X2.EMV.
Screenshot:
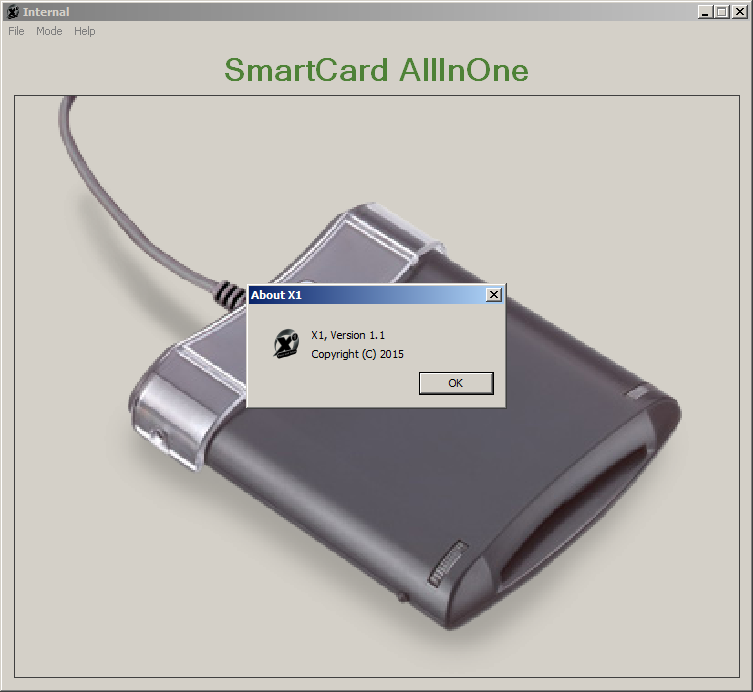
Mirror provided by vx-underground.org, thx!
(infected)
SHA-1: 4c740df32ceb14e93294855d124b47440a558571
File type: EXE/Windows
File size: 2.19 MB
File name: Internal.exe
ProtectionID:
CvSig : 0x53445352 | SigGuid ADBF2837-3F60-4019-B1CD0144ED27A69F
PDB/VBP pathway: g:\dev\_current\smart card reader\X1_software\softwares\internal full\Src\X1\Release\X1.pdb
Compilation date: 2015-08-08 16:30:16
First seen: 2015-08-08 16:30:16
Name: X1 v1.1
Additional note: Code: cf4ac1badfd87b60e9e81987a9959a18a6791c9ba5070e7980efd624dc75bc38.
From the same family: X1 v1.1, X1 Toronto.
Cosmetic reshacks from the 'x2 cartel':
X1 v4.1, X1 v5.0, X2G, X2A, X2A (nfc design), X2A (mr_emv trial), X2A Cracked, X2, X2.EMV.
Screenshot:

Mirror provided by vx-underground.org, thx!
(infected)
...83fab200.zip
21-10-24
...b928e1f7.zip
21-08-07
...be8a79c9.zip
21-07-17
...0393ebfd.zip
21-06-12
...c6a1ec78.zip
21-06-05
...b2fefd36.zip
21-05-23
...b58f906f.zip
21-05-22
...8c55884d.zip
21-05-22
...a4cbe72a.zip
21-05-21
...6472a452.zip
21-05-18
...be8a79c9.zip
21-07-17
...83fab200.zip
21-10-24
...b928e1f7.zip
21-08-07
...0393ebfd.zip
21-06-12
...c6a1ec78.zip
21-06-05
...f2874124.zip
14-09-04
...c7ebe762.zip
18-01-19
...8c55884d.zip
21-05-22
...b2fefd36.zip
21-05-23
...b58f906f.zip
21-05-22
MOST ViEWED NOTiCE
EMVToolUltimate v1.0
8150
CATR 3.8.7
7328
X2 v2.8
6217
ATRToolUltimate 1.0
4442
POS Simulator 2.0
4056
ATRtool v2.0
4014
Emvfoundry v1.0.0.63
3761
POS Simulator 2.0
3082
X2.EMV
2871
emvfoundry v1.0.0.54
2563
Daphne
2372
Emvfoundry v1.0.0.19
2364